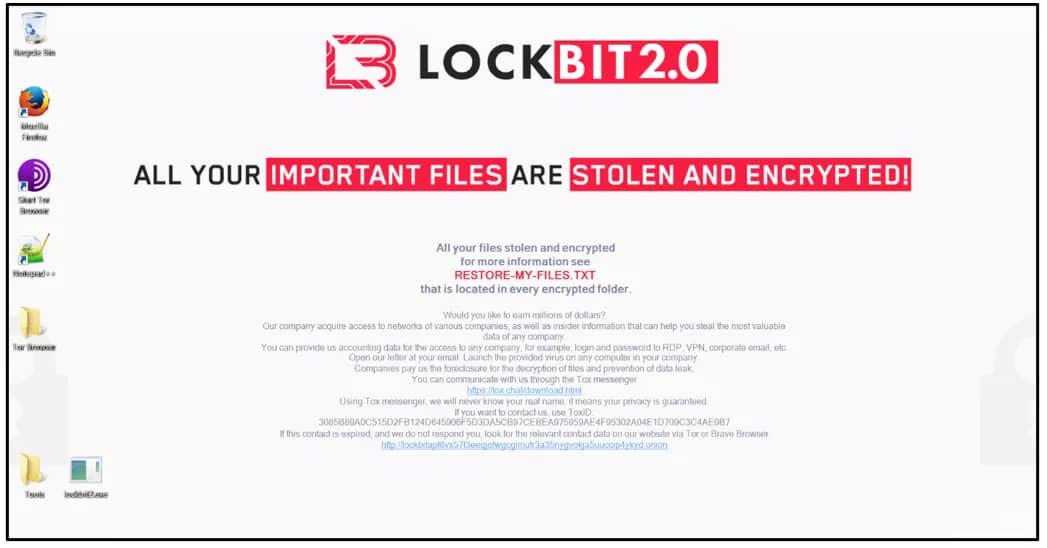
The creators of LockBit ransomware were covertly developing a new iteration of their file-encrypting software, named LockBit-NG-Dev, possibly intended to be released as LockBit 4.0, before government police dismantled the cybercriminal’s network earlier this week.
Trend Micro, a cybersecurity business, assessed a sample of the latest LockBit development capable of functioning on various operating systems as a result of collaborating with the National Crime Agency in the UK.
The current LockBit malware sample is a work-in-progress written in .NET and compiled using CoreRT, and packed with MPRESS, unlike the previous versions that were produced in C/C++.
Trend Micro reports that the virus contains a configuration file in JSON format that specifies the execution parameters, including the execution date range, ransom letter contents, unique IDs, RSA public key, and other operational settings.